Pearl Echo
 Pearl Echo is a comprehensive Internet monitor and Web filter that can be used across multiple areas including web surfing, e-mail, file transfers, social media and instant messaging. Pearl Echo provides cybersecurity for users in single or multiple locations as well as roaming and mobile Internet users.
Pearl Echo is a comprehensive Internet monitor and Web filter that can be used across multiple areas including web surfing, e-mail, file transfers, social media and instant messaging. Pearl Echo provides cybersecurity for users in single or multiple locations as well as roaming and mobile Internet users.
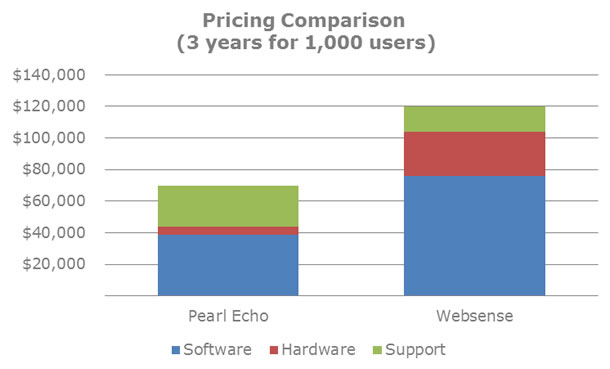
Cybersecurity Product Comparison
|
Pearl ECHO |
Websense |
License |
Own |
Subscription (pay or disable) |
| URL Database | Yes |
Yes |
| Real-time Threat Scan | Yes |
Yes |
| Real-time Updates & Overrides | Yes |
No |
| Crypto.View | Yes |
No |
| Safe Search Enforcement | Yes |
Yes |
| Integrated Remote Monitor | Yes |
No |
| Real-time Monitor | Yes |
Yes |
| E-mail and IM Content Restore | Yes |
No |
| Requires Traffic through Appliance | No |
Yes |
| Scalable Architecture | Yes |
No |
| Secured Endpoint | Yes |
No |
| Comprehensive Reporting | Yes |
Yes |
| Total Cost of Ownership | Low |
High |
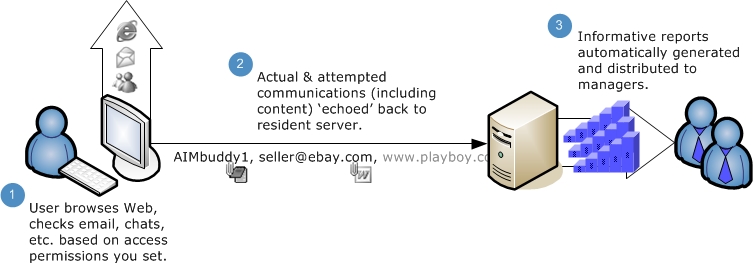
How it Works
Pearl Echo’s patented cybersecurity technology is based on an independent agent-server architecture. The Echo agent monitors and controls all Internet traffic based on rules created at the Echo server. Pearl Echo does its job regardless of which Internet application is being used. Echo is not reliant on proxies or firewalls and is not affected by high traffic volumes, how users access the ‘Net or where they are physically located.
Pearl Echo benefits over Websense
Ease of Administration and Installation
- Software was initially developed for Technical Administrators with little or no network experience.
- Demonstration installation up and running in ten to fifteen minutes.
- Not a plug-in solution so has no negative parasitic effect on network performance or your ability to evolve your network.
- Centralized administration of workstation agent deployment.
Strong Software-Only Approach
- Easy to install and evaluate product without any cost or network configuration change.
- No requirement to purchase and maintain an appliance.
- No rerouting of Internet traffic through an appliance or series of sniffers.
- Full visibility into encrypted traffic.
- Goes beyond Web filtering and monitors and controls popular Internet protocols, bandwidth and applications.
- No modification of existing network architecture.
- No bottleneck considerations on client or server. Network traffic continues to flow on the path that you designed.
- No single point of failure that kills connectivity.
- No ongoing maintenance – product is self updating.
- Simple to add new modules and new users by changing serial number and adding software agent to new endpoints.
Pricing
- Meet or Beat (based on three year comparable configuration).
- Buy and own the software. No required ongoing subscription costs.
- Maintenance is optional - has strong benefits but products will continue to function if not purchased or renewed if budget does not permit.
- Web category filtering module is optional based on filtering requirements and is optionally renewable subsequent years for only $1.20 per license per year.
- Purchase the amount of licenses needed, not an arbitrary block or quantity.
- Add on licenses via simple change of serial number.
Design Architecture
- Product natively manages mobile users, Citrix and Terminal Server environments, multiple locations and remote offices. No shims or cumbersome workarounds required.
- Highly secure and, unlike competition, cannot be easily circumvented by going off-network.
- Easy full deployment roll-out with no-touch automated installation procedures.
- Highly scalable agent-server architecture.
Evaluation Download
Download and test a two hundred fifty(250) user license of Pearl Echo.Suite:

