A Targeted Cybersecurity Solution for Web Filtering
Website.Echo manages web site traffic based on protocols that all Web browsers use to communicate with Web servers. Since all Internet browsers conform to this standard, Pearl Echo seamlessly monitors, filters and controls any compatible browser. Website.Echo is not effected by browser application changes since it applies cybersecurity at the protocol level. Website.Echo provides advanced Internet monitoring, filtering and management capabilities allowing you to enhance productivity and protect and conserve resources. Pearl Echo's patented cybersecurity technology enables you to maintain the continuity of your web access usage policies beyond your company’s internal network.
Enterprise-Ready
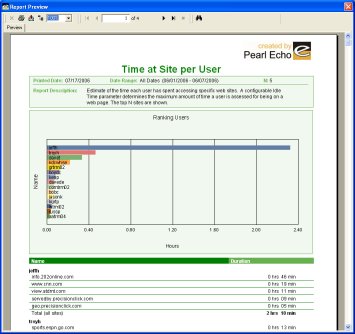
Website.Echo was designed with the enterprise in mind. The Website.Echo Report Manager consists of over forty standard reports that can be customized for your existing Domain users and groups. The Website.Echo Report Manager allows users to run reports interactively or to schedule reports to be automatically generated and distributed. For larger data handling and analytic needs, Website.Echo easily integrates with MS SQL Server. If your organization includes a server-centric computing environment, keep in mind that Website.Echo is the only web access management software that is certified and fully functional in a Citrix/ Microsoft Terminal Services environment.Grows with your Business
Website.Echo is packed with features for the large enterprise but remains targeted to the core needs of your growing business. Features like automated deployment, an intuitive standards-based administration console, server-optional setup and self-administering workstation agents allow Website.Echo to meet the needs of any size organization.Protects
Website.Echo features a keyword and text pattern blocking option which helps safeguard against the dissemination of personal or confidential information entered during a browser session. Website.Echo acts as the enforcement behind your organization's cybersecurity policy. All communications can be archived for rapid retrieval, protecting organizations from laws suits related to discrimination-based claims and regulation compliance.
Secures
Website.Echo provides a secure installation option to protect against unauthorized circumvention. Website.Echo is so efficient that users notice no degradation of access speeds and detect no obvious process or files on their workstations.Controls
In addition to the Echo.Filters URL category database, Website.Echo provides administrator-defined Allow and Block lists for instances where user content access needs to be limited. Pearl Echo also allows you to set various Internet access profiles based on time of day - perfect when you need to provide some flexibility for your day-extenders.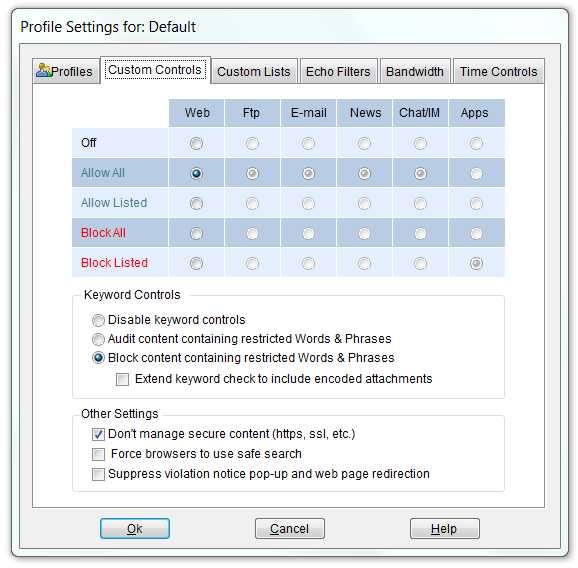
Provides Complete Flexibility
Managed users can be connected to your local area network, wide area network, or be completely detached from your private network. Website.Echo runs as an independent service eliminating reliance on legacy proxy servers or integration issues with firewalls or multiple subnets. Website.Echo's architecture scales well and allows you to monitor any form of Internet connection - anywhere. Website.Echo applies cybersecurity rules by user, group and computer names. Administration is streamlined by optionally integrating into your Windows Domain or Stand-alone server structure. Unlimited cybersecurity Profiles can be created to provide varying levels of management for your existing Directory users, groups and computers.
Download a Free Trial ...to get a hands-on look at Pearl Echo's features and functions
Start the Pearl Echo.Suite Product Video Tour ...to get a quick look at Pearl Echo's capabilities without installing.
View Pearl Software vs. Competition ...to see how Pearl Software stacks up to the competition.
Request a Quote ...to receive personalized pricing that matches your requirements.
